Advanced Persistent Protection - Taking Security to the Maximum Level
We help organizations to become more secure in face of cyber attacks by reducing risk and exposure
Contact Us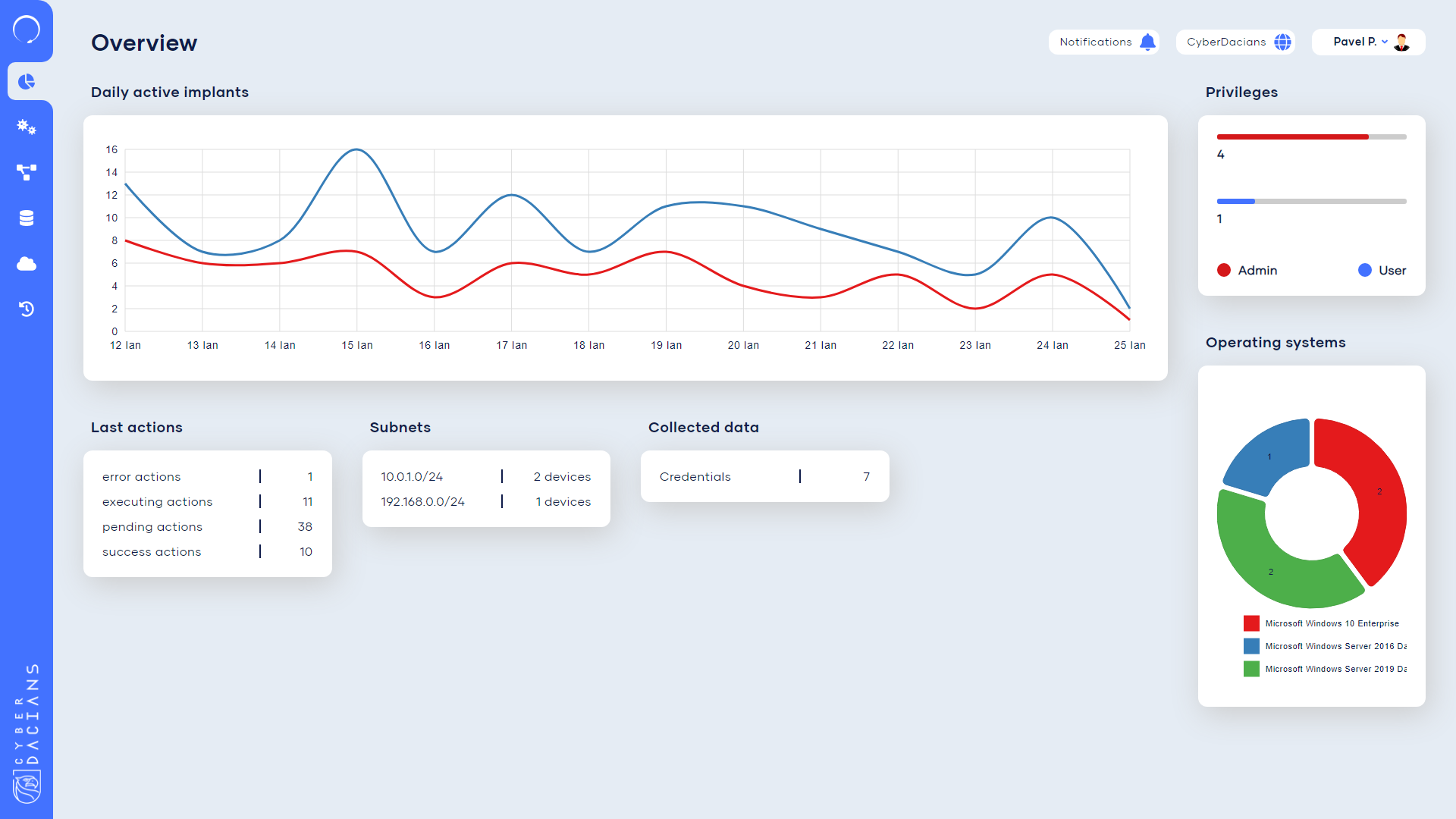
Cyber attacks are growing extraordinarily complex and the security ecosystems of most companies are not keeping up with the attacks.
Employ in a safe manner Advanced Persistent Threat (APT) techniques to test the response of the security controls
Identifying breaches in infrastructure that can lead to a cyber attack and offering recommendations on fixing them
Maximize the effectiveness of your security program
Test the quality of your current cybersecurity investments and get the full benefit of them
Test the new cyber attack strategies employed by APTs to check if your infrastructure can be affected by an attack and constantly update configurations to sustain the attacks
Find the ways attackers can move through your networks in order to be able to restrict and monitor the movements.
Maximize the impact of your cyber capabilities, processes and people through coordination between the red team and the blue team
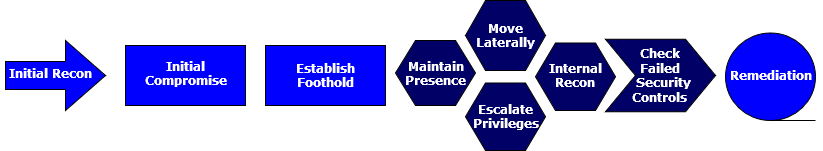
StageOne is an adversarial attack simulation framework designed to emulate the modus operandi of Advanced Persistent Threats based on MITRE ATT&CK™, which is a globally - accessible knowledge base of adversary tactics and techniques based on real-world observations. The ATTACK knowledge base is used as a foundation for the development of specific threat models and methodologies in the private sector, in government, and in the cybersecurity product and service community.
When StageOne is deployed in the security infrastructure, it continuously tests different security measures in order to validate security controls using attack emulations. These emulations assist Red and Blue Teams to measure the effectiveness of security controls and find the gaps existent in the infrastructure before a hacker does it.

Ready to test your defenses?
An implant designed to be infiltrated in the infrastructure
The Command & Control Center which controls the implant
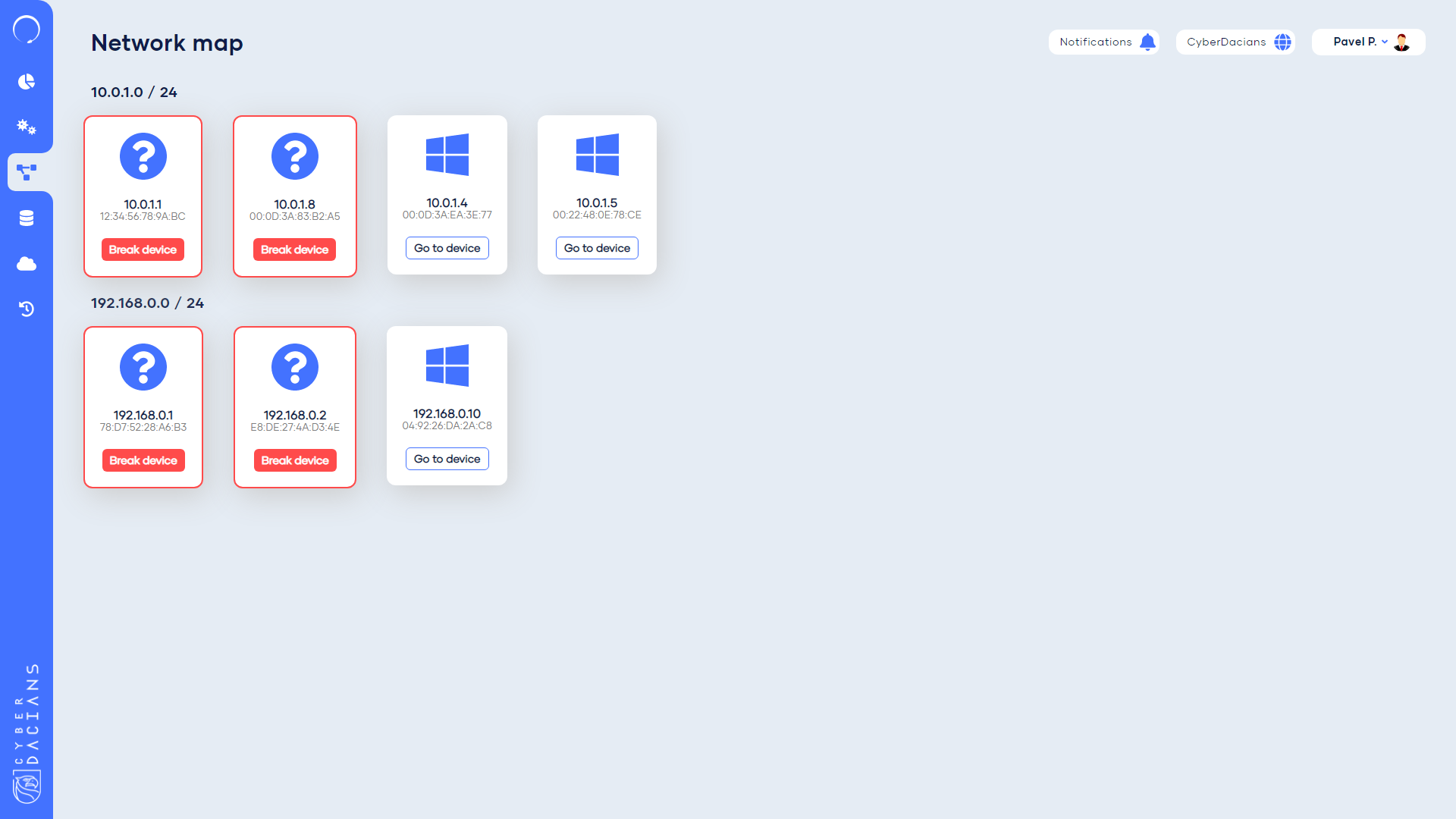
Stageone dashboard offers a centralized place to see all the computers and the network map of them. The lateral movement procedure is done via this panel by “breaking into a device.”
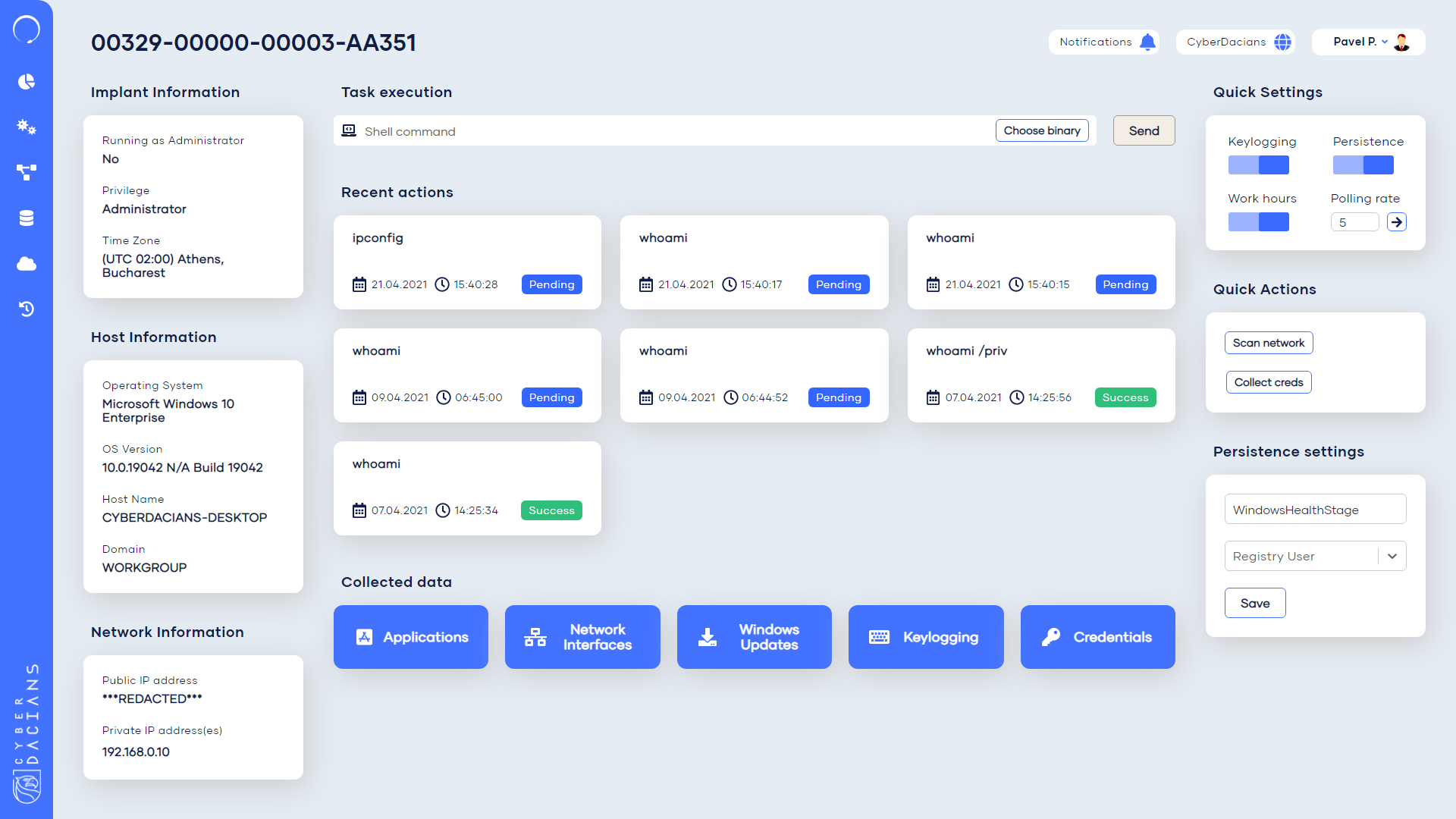
This page offers a comprehensive view over an implant. It displays various general information and configurations and a main view over the recent executed tasks. The collected data panel is at the bottom and offers a great insight into the penetrated device.
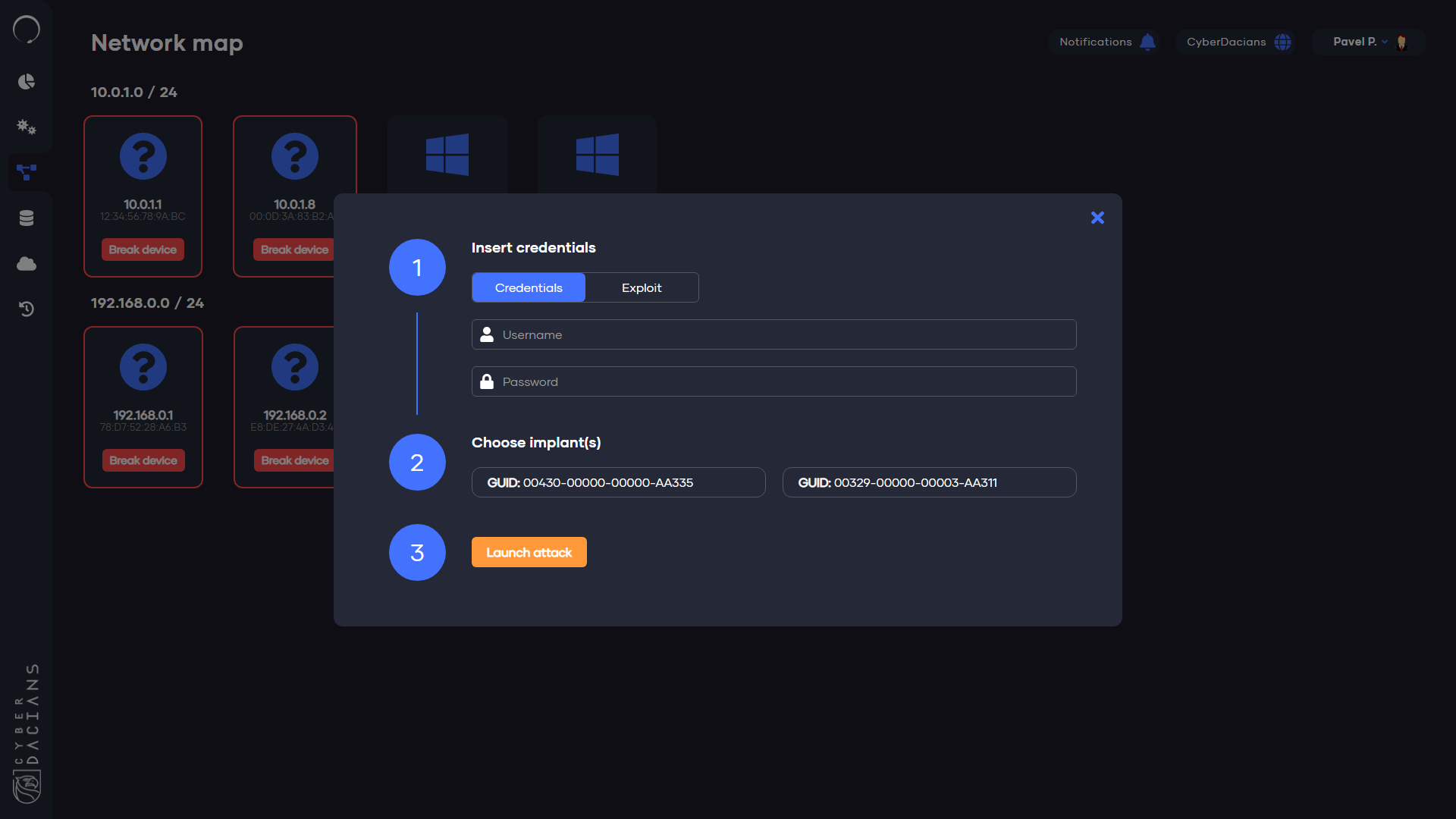
The lateral movement popup allows us to move laterally through the network and displays a few options to choose from, such as Credentials and Exploits. After choosing one implant to carry the attack, the penetration is ready to go.
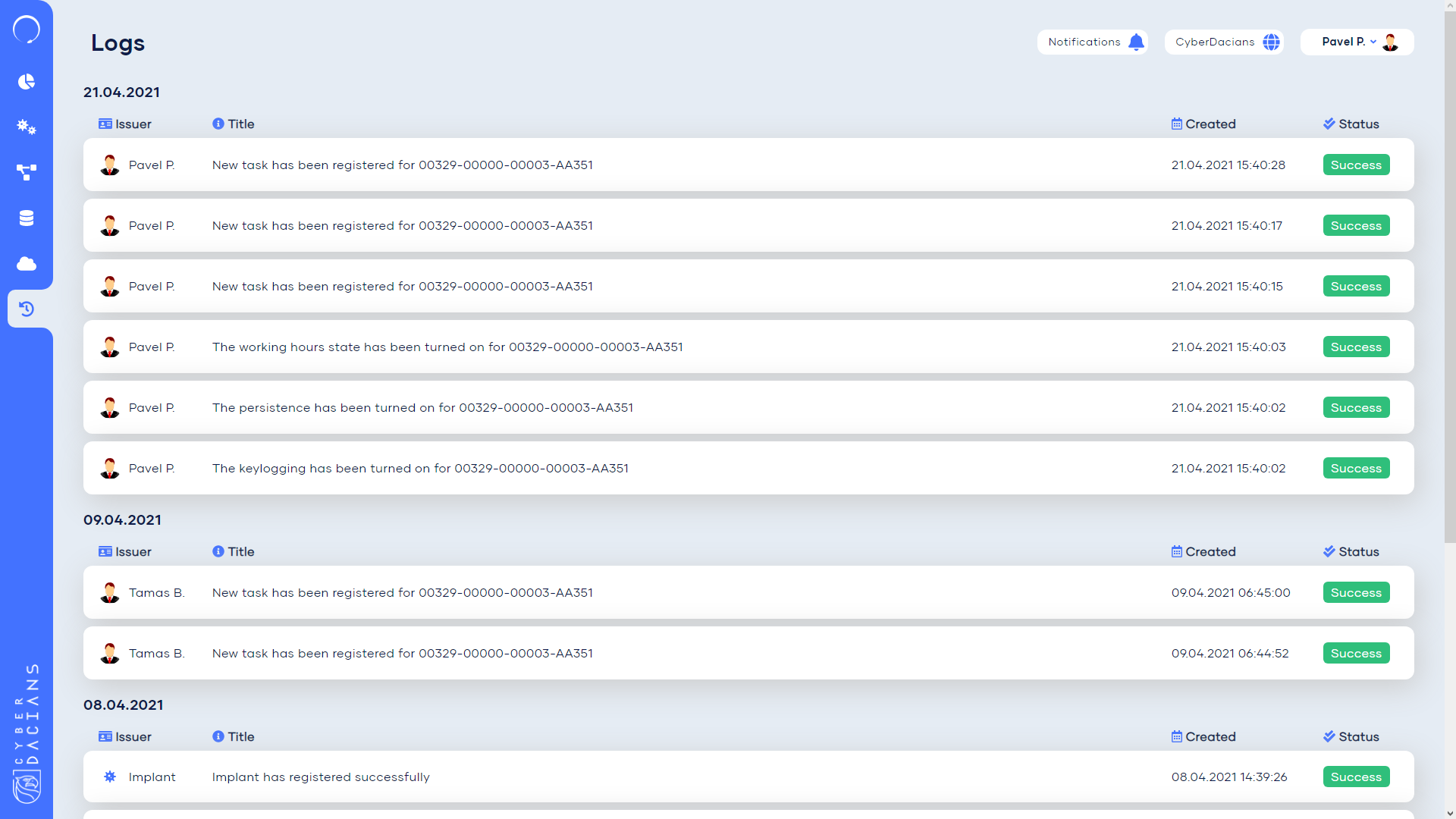
Logs are always important. StageOne dashboard offers a comprehensive view of what’s going on into the system and keeps track of all the movements of the implant.
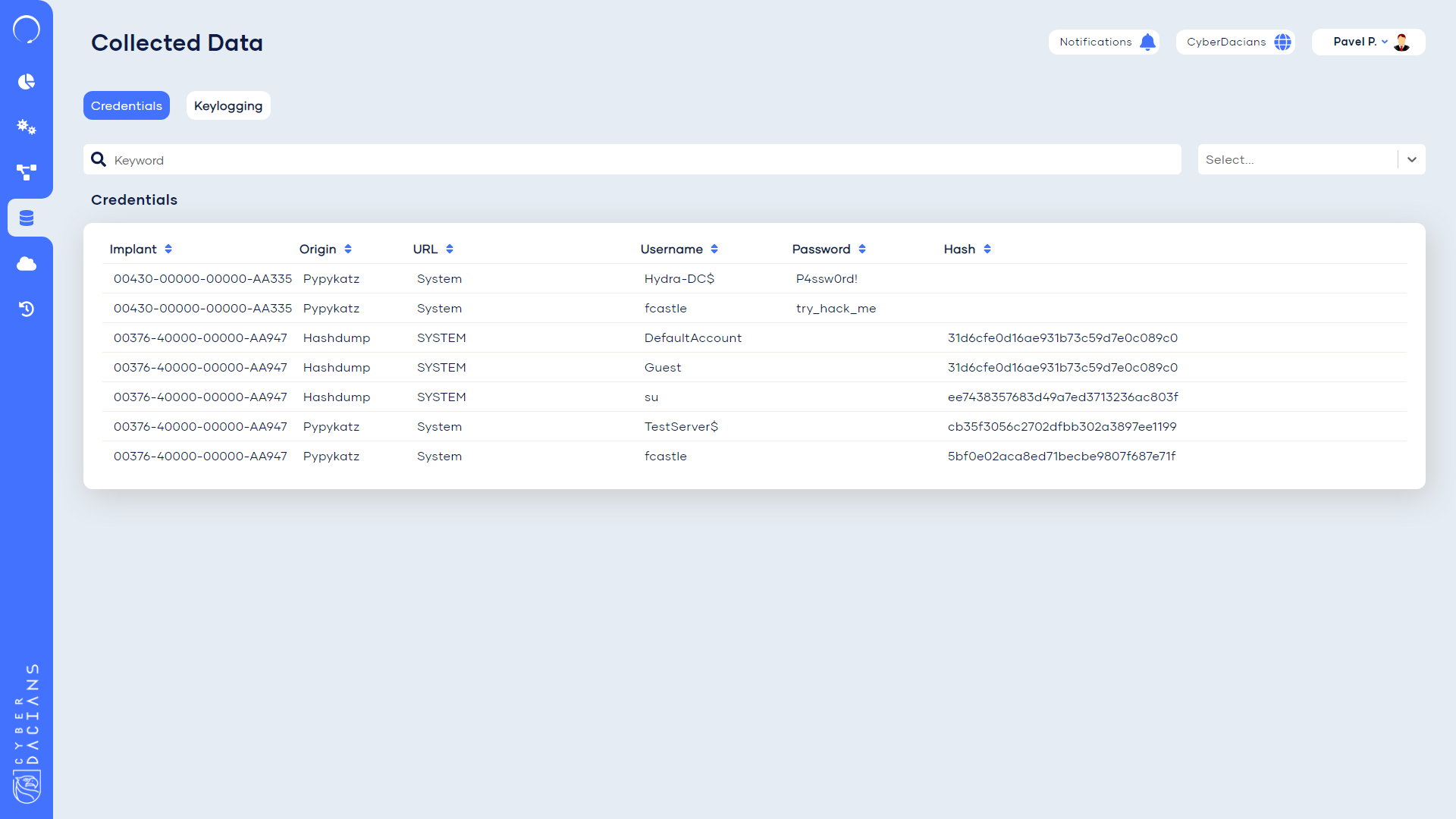
The collected data page centralizes all the credentials extracted and the keylogging from the systems they were active.
This is a special page which allows the operator of stageone to configure campaigns and users.